
If you look at the numbers for video conferencing and team messaging apps before and after the pandemic began, you’ll see the explosion of the necessity for virtual communications. [Read more…]

If you look at the numbers for video conferencing and team messaging apps before and after the pandemic began, you’ll see the explosion of the necessity for virtual communications. [Read more…]

In 2021, we saw quite a few supply chain attacks. These attacks are so dangerous because there is a chain reaction when one particular company is attacked. Instead of the attack impacting just that company, it has a much wider effect. [Read more…]

Alongside the rise in the number of people working remotely on a regular basis, has been the increasing popularity of software designed to track employee productivity. [Read more…]

Access management continues to get more complicated as more cloud tools get added into business workflows. For each SaaS application being used by a company, on the backend, there are users that must be added and a permission level decided upon. [Read more…]

The problems with password security are well known. People gravitate naturally toward creating passwords they can easily remember and will use those same passwords over multiple accounts. This makes them easy to breach. [Read more…]

One problem that continues to plague the cybersecurity efforts of multiple organizations is that employees have too many passwords to manage. The average person has at least 100 different passwords that they use regularly and has to keep up with. [Read more…]

Today’s forms of malware are designed to spread quickly to as many connected devices as possible. Once a hacker infects one computer, server, or mobile device, automated code seeks out network connects and looks for any other places it can spread. [Read more…]

One of the biggest threats that companies need to defend against is phishing. These socially engineered messages come to employees in multiple forms and are getting more sophisticated every year. [Read more…]
You’re likely already familiar with the terms two-factor authentication (2FA) and multi-factor authentication (MFA). These are two different terms for the same process of requiring an additional step before granting access to an account.
This is a standard of good cybersecurity hygiene and helps prevent a costly breach of a cloud account or remote access login.
2FA/MFA will typically be implemented in one of three ways:
The key with multi-factor authentication is that it requires someone to have access to a physical device that receives the time-sensitive code. This is often the thing that stops hackers from gaining access to an account, even if they have the username and password.
In a Google study, MFA was found to be between 76% and 100% effective at blocking account takeover attempts, depending upon the type of MFA used and the attack type.
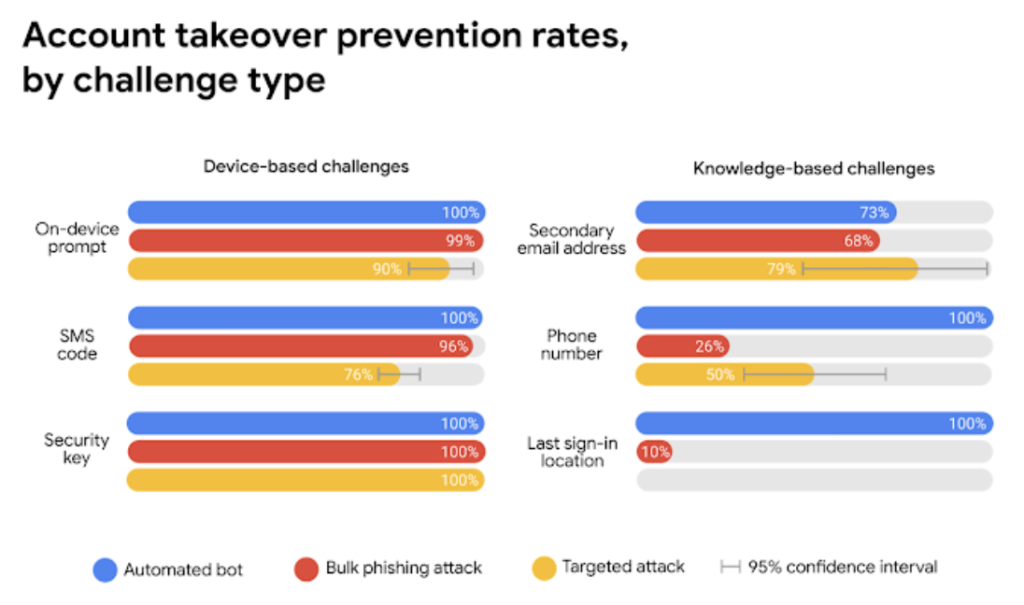
Graph from Google MFA Study
2FA/MFA can significantly improve data security for multiple types of accounts, including for network-attached storage (NAS).
Network-attached storage is a data storage device that is usually kept onsite. It’s used as a type of “mini-server” and is designed for storing files and running certain types of applications that allow files to be shared easily.
Companies use NAS to maintain more control over their file storage than they may have if relying on a cloud-storage provider. It enables the files to be available both online and offline.
The benefit of using NAS is that it’s a hybrid of both cloud and hard drive storage. It allows access by multiple people and devices from any location. It’s typically less expensive than a full server because it’s designed mainly for file storage and sharing only.
It can be connected to, directly through an ethernet connection or a direct USB-to-computer cable. Approved users can also log in and connect to NAS remotely, just like they can cloud storage services.
NAS holds a lot of sensitive data and files. Because it’s accessible online through a user log in, it’s susceptible to being hacked if you don’t have strong account protections.
Particularly dangerous files for a hacker to gain access to include business financial and tax records, customer records, employee payroll data, and research and development information on products.
2FA significantly reduces the risk of falling victim to a breach of your NAS device by raising the bar for access.
According to Verizon’s Data Breach Investigations Report (DBIR), on-premises assets are much more likely to be breached than cloud assets. On-premises devices like servers and network-attached storage are involved in approximately 70% of data breaches, while cloud assets are involved in just 24% of them.
This is because large cloud storage platforms are run by companies like Microsoft, Google, and Dropbox, and are much more difficult to breach. On-premises assets are usually easier because they often lack important security safeguards, such as MFA.
Credential theft is on the rise and is now the number one cause of data breaches around the world. Hackers are targeting user credentials because it’s the easiest way to breach security on an account and gain access to things like business email and files containing data that can be used for identity theft.
As we’ve noted above, 2FA/MFA is very effective at stopping hackers in their tracks when they try to breach your username and password. It’s a simple and affordable (free in most cases) way to significantly improve the security of your NAS so you can enjoy flexibility and anywhere access without having to worry about a breach.
Implementing 2FA/MFA on a NAS device is easy. You will typically visit your account settings and look for an area that notes access or password management. You’ll then enable the 2FA or MFA option.
Some NAS devices will ask you to enter a mobile number for sending the MFA code. Others may have their own authentication app for you to download and set up. If you have multiple users, make sure that each one goes through the MFA setup process, so your accounts are all properly secured.
Don’t leave your accounts unprotected. Connect2Geek can help your Treasure Valley area business with account access security that’s simple to implement and keeps your NAS and other accounts protected.
Schedule your free consultation to learn more today! Call 208-468-4323 or reach out online.

One statistic that stood out on the most recent IBM Security Cost of a Data Breach Report was connected to credential theft. Compromised usernames and passwords are now the #1 cause of data breaches, and account for 20% of them globally. [Read more…]
