
How do you think your team would do in a phishing simulation test? Approximately 97% of users can’t recognize a sophisticated phishing email, and only 3% of employees report phishing emails to their company.
Phishing is dangerous at both home and work. A well-disguised fake that looks like a credit card offer from your bank can trick you into compromising your online banking details or providing your SSN.
The number one driver of data breaches and malware infections for organizations is phishing. It’s one of the most challenging threats that compromise network security because it directly targets company users.
While it’s important to have software safeguards in place like DNS filtering, email authentication, and up-to-date antivirus, you can’t stop with those tools when it comes to fighting phishing. You need to have strong user awareness training to help sharpen those detection skills.
One trick for improving phishing identification is to use the SLAM Method.
Using SLAM to Improve Phishing Identification
SLAM is an acronym for four areas of an email message that you should check before taking action on any suspicious or unexpected email. Even an email that seems legitimate can be a clever fake.
These four areas are:
- Sender
- Links
- Attachments
- Message
Scammers will spoof email addresses so they appear to be from senders you may do business with. They’ll also copy real emails from companies like Amazon or Bank of America, right down to the company signature.
Using SLAM helps you remember to stop and stay before reacting to an email. If you take a moment to carefully look over those four key areas of a message, there is a much bigger chance that you’ll spot a fake and won’t mistakenly click a malicious email link.
Let’s take a closer look at the things you should check using SLAM.
Sender
You can’t just trust the name you see in the sender line of an incoming message. Hackers will often spoof emails in two ways:
- Use the email domain of another company even though the email wasn’t sent from them
- Use part of the real company name with another email address that looks like it could be legitimate
If your server doesn’t have email authentication enabled, then you might receive an email that looks like it’s from a colleague, but actually came from a phishing scammer that is spoofing your domain. If you ever receive a curious email from a colleague, friend, or company you do business with, it’s best to contact them directly (not by replying to the email) to ask if it’s legitimate.
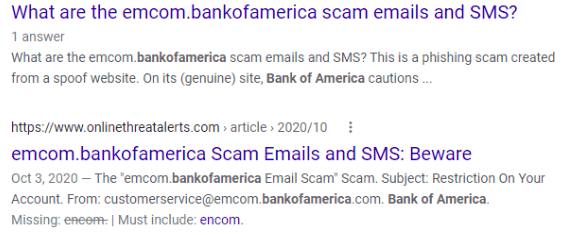
Below is an example of how a clever phishing campaign will use an email address that most users would think is legitimate. It uses “bankofamerica@emcom.bankofamerica.com.”

The email looks real and uses all the BOA graphics. But a quick search on that email address shows that it’s actually a clever scam.
Links
Phishing emails now use URLs more than they use file attachments to spread malware or steal user login credentials. Links often seem innocuous to users, but they can be just as dangerous as a file attachment.
You should always hover over links without clicking on them to see where they are taking you. Malicious links can also be spoofed to look similar to legitimate websites, so make sure to check for any spelling errors.
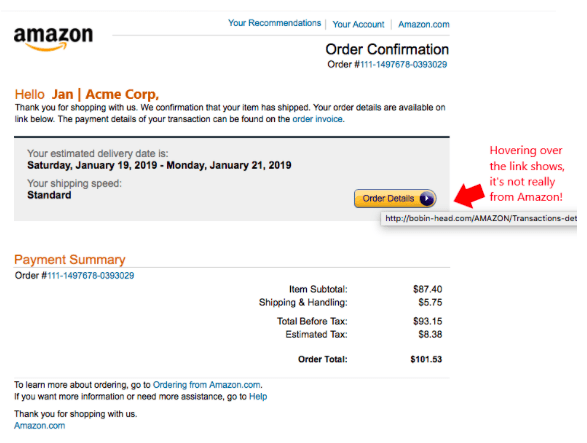 Many phishing emails spoof other companies like Amazon or USPS. When you click the link in the email, it will even appear as if you are at the right login page. It will be spoofed to look like the real thing. Once you enter your login details, the attacker has them!
Many phishing emails spoof other companies like Amazon or USPS. When you click the link in the email, it will even appear as if you are at the right login page. It will be spoofed to look like the real thing. Once you enter your login details, the attacker has them!
It’s best when checking shipment tracking, order receipts, or anything else, to go to the site directly rather than using an email link to get there.
Attachments
File attachments continue to be used in some phishing campaigns, but scammers are getting better at hiding malicious files. For example, instead of sending something that most users will think is a red flag (like a .tar file), they will send a trusted file format like a PDF or Word document. But these file types can also be weaponized with malware.
Always have attachments scanned by antivirus/anti-malware software before opening them. Never open any file attachments from unknown senders.
Message
Finally, you want to check the body of the message carefully for anything that seems “off.” This could be a message that doesn’t sound like it’s from the person it’s pretending to be from, or it could be grammatical errors or typos.
While phishing emails have become much more sophisticated, so it’s harder to spot these types of errors, they do still exist if you look carefully.
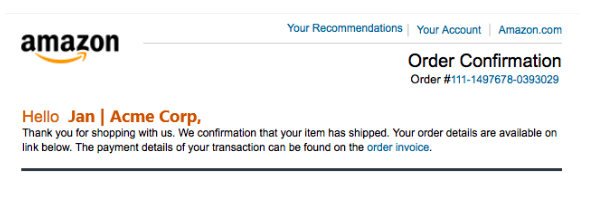
For example, when you zoom in on the Amazon order phishing email you can see a grammatical error in the second sentence. It says, “We confirmation that your item has shipped” instead of “We confirm that your item has shipped.”
Read the text of suspicious emails carefully to catch these types of mistakes.
 Improve Your Phishing Detection Software & Awareness
Improve Your Phishing Detection Software & Awareness
Connect2Geek can help your Treasure Valley area business with effective safeguards against phishing attacks that include both software protections and employee awareness training.
Schedule your free consultation to learn more today! Call 208-468-4323 or reach out online.

 Improve Your Phishing Detection Software & Awareness
Improve Your Phishing Detection Software & Awareness